JTAG Debug Enable Signals
Introduction
In modern ARM-based SoCs, JTAG debug access is a key mechanism for software development, system validation, and manufacturing test. However, enabling JTAG is not as simple as toggling a single pin. Multiple hardware debug enable signals exist to control:
- Which security domain is accessible (Non-Secure vs. Secure)
- What type of access is allowed (Invasive vs. Non-Invasive)
- Which resources can be accessed (CPU registers vs. system memory)
These signals are critical for enforcing SoC security policies and controlling debug capabilities throughout the device lifecycle.
CoreSight Access Overview
ARM CoreSight architecture defines two main debug paths:
| Access Type | CoreSight Component | Capability |
|---|---|---|
| Register access | Core Debug / APB-AP | Halt CPU, read/write CPU registers |
| Memory access | AHB-AP / AXI-AP | Read/write system memory and peripherals |
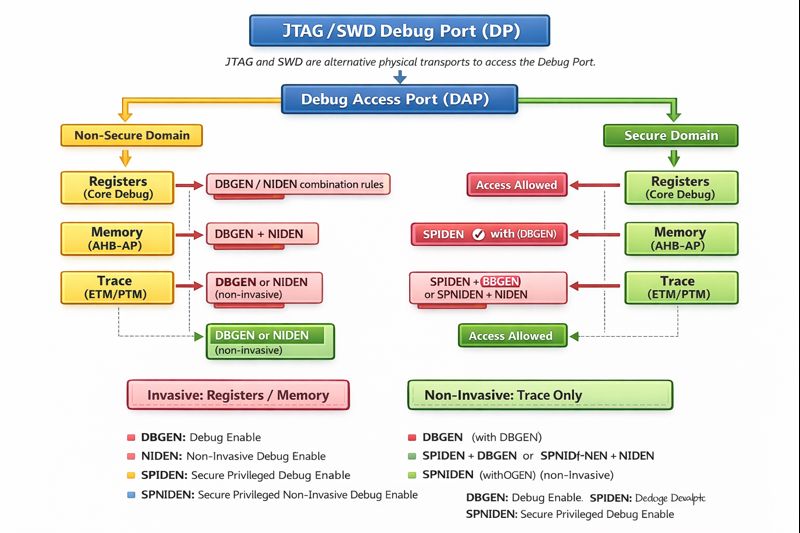
Access to these components is controlled by debug enable signals such as DBGEN, nIDEN, SPIDEN, and SPNIDEN.
Debug Enable Signals
Non-Secure Debug Signals
These signals control access to non-secure debug resources:
| Signal | Active State | Purpose |
|---|---|---|
| DBGEN | High | Enables non-secure debug |
| nIDEN | Low | Enables invasive debug globally |
Implications:
- Non-secure JTAG debug (register + memory) requires
DBGEN - Memory access via AHB-AP additionally requires
nIDEN - Used in development for CPU halt, single-step, and memory inspection
Secure Debug Signals
These signals control access to Secure world debug resources:
| Signal | Active State | Purpose |
|---|---|---|
| SPIDEN | Low | Secure invasive debug (halt CPU, modify registers/memory) |
| SPNIDEN | Low | Secure non-invasive debug (trace / observation only) |
Implications:
SPIDENis required for Secure memory or register accessSPNIDENallows trace and monitoring but does not allow memory writes or CPU halt
Memory Access Signals
Memory access via AHB-AP or AXI-AP is always considered invasive debug:
| Domain | Required Signals | Notes |
|---|---|---|
| Non-Secure | DBGEN + nIDEN | Allows read/write of non-secure RAM, flash, peripherals |
| Secure | SPIDEN + nIDEN | Allows read/write of secure RAM, flash, peripherals |
SPNIDEN does not enable memory access.
Register Access Signals
Register access is domain-specific:
| Domain | Required Signals | Access Type |
|---|---|---|
| Non-Secure | DBGEN (+ nIDEN for invasive) | CPU halt, read/write registers, single-step |
| Secure | SPIDEN | CPU halt, read/write secure registers |
Trace and Observation Signals
Non-invasive observation via ETM, PTM, or trace funnels requires:
| Domain | Required Signals |
|---|---|
| Non-Secure | DBGEN |
| Secure | SPNIDEN |
Trace access does not allow memory modification or CPU halt.
Consolidated JTAG Enable Matrix
| Domain | Access Type | CoreSight Path | Required Signals |
|---|---|---|---|
| Non-Secure | Register | Core Debug | DBGEN (+ nIDEN for invasive) |
| Non-Secure | Memory | AHB-AP | DBGEN + nIDEN |
| Secure | Register | Core Debug | SPIDEN |
| Secure | Memory | AHB-AP | SPIDEN + nIDEN |
| Non-Secure | Trace | ETM / funnels | DBGEN |
| Secure | Trace | ETM / funnels | SPNIDEN |
Debug Signal Policy Across Device Lifecycle
JTAG and debug enable signals are usually configured differently at each lifecycle stage to balance debug capability and security.
| Lifecycle Stage | DBGEN | nIDEN | SPIDEN | SPNIDEN | Notes / Access Scope |
|---|---|---|---|---|---|
| Development | 1 | 0 | 0 | 0 | Full debug access to non-secure and secure domains. Enables invasive memory and register access, as well as trace. Used for silicon bring-up, software development, and validation. |
| Production | 0 | 1 | 1 | 1 | All invasive debug disabled. Trace may also be disabled or limited. Ensures secure firmware and data cannot be accessed or modified externally. |
| RMA / Failure Analysis | 1 (sometimes limited) | 0 (partial) | 1 (secure invasive disabled) | 0 (secure trace may be enabled) | Controlled re-enablement of non-secure debug for analysis, while secure invasive access remains blocked. Often requires authorization or hardware keys. |
| Field / Customer | 0 | 1 | 1 | 1 | Debug fully disabled to prevent unauthorized access. May allow only trace under very limited circumstances, depending on SoC design. |
Visual Diagram: JTAG Access Gated by Debug Enable Signals
Key Takeaways
- Enabling JTAG is signal-dependent, not just pin-dependent.
- Memory access requires invasive debug signals (
nIDEN,SPIDEN). - Register access is domain-specific and may require both invasive and non-invasive enables.
- Trace-only access is non-invasive and controlled separately (
SPNIDENfor secure,DBGENfor non-secure). - Proper gating ensures security throughout development, production, RMA, and field deployment.
By understanding the role of these signals and their lifecycle policies, engineers can design secure, debuggable ARM-based systems without exposing sensitive resources to unauthorized access.